-
随着互联网和多媒体的迅猛发展,信息安全领域面临着越来越多的挑战。光学信息安全技术由于其并行性、快速和高加密维度等特点,正在信息安全领域发挥着越来越重要的作用。在该领域众多的加密系统中,REFREGIER与JAVIDI提出的双随机相位编码系统 是最引人注目的,该加密技术采用4f系统来实现:把两块随机相位掩模分别放入系统的输入平面和傅里叶频谱面,对原始图像的空间信息和频谱信息做随机编码,这样可以将输入的图像编码成复平稳的白噪声[1-6]。该系统衍生出来的基于菲涅耳域的双随机相位编码加密系统,该加密系统最大的特点是有两个可变换参量,菲涅耳变换相比于其它变换具有更高的安全性,并且不需要光学透镜,与此同时,两块相位板、衍射的距离和波长都可以成为密钥,增加密钥的容量,可控性强[7-8]。
目前,随着互联网技术的迅速发展,数字图像信息量与有线网络的传输能力相互制约,因此,图像的压缩与加密成为了实际应用的研究热点。为了解决图像加密后的传输效率,人们对加密系统的容量要求变得越来越高[9-12]。于是一些图像加密与压缩的光学加密算法相继出现。比如,LIN等人提出了一种基于混沌的图像压缩加密算法[13]。XU等人提出了离散余弦变换与脱氧核糖核酸运算相结合的图像压缩加密算法[14]。虽然这些算法都可以对图像进行压缩与加密,且具有较好的加密效果,但是加密的安全性需要进一步提高。然而这些加密方法将多图像压缩成复合图像时,易产生串扰,导致解密时,图像失真较大,解密质量不佳等特点。
为了解决图像加密后,数据量大且传输速率慢的问题,本文中先利用光学小波变换[15]对多幅彩色图像进行压缩然后利用菲涅耳变换来加密图像信息。本文中的加密算法不仅具有传输速度快、占用空间小的优点,同时还能使图像加密效果得到显著提高,保证了图像加密后安全性高。仿真结果表明,相比于其它图像压缩加密算法,该算法在面对统计分析、噪声攻击、以及裁剪攻击等手段时,具有很好的鲁棒性。
-
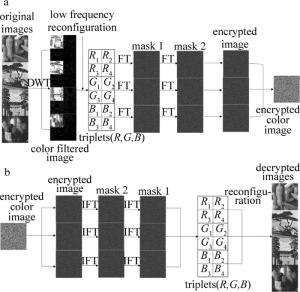
本加密方法结合了离散小波变换和菲涅耳变换。为了阐述该加密方法,图 1是本方法的加密过程和解密过程的系统图。图中, DWT是离散小波变换(dis-crete wavelat transform), FT表示菲涅耳变换(Fresnel transform), IFT表示菲涅耳逆变换(inverse Fresnel transform)。
-
对于2维信号f(x, y),若母小波函数为h*(x, y),则f(x, y)的小波变换可描述为:
$ \begin{align} &{{\mathit{\boldsymbol{W}}}_{f}}\left( {{u}_{1}}, {{u}_{2}}, {{v}_{1}}, {{v}_{2}} \right)=\text{DWT}\left[ f\left( x, y \right) \right]= \\ &\ \ \ \ \left[ f\left( x, y \right), {{h}^{*}}{{_{{{u}_{1}}}}_{, {{u}_{2}}, {{v}_{1}}, {{v}_{2}}}}\left( x, y \right) \right]= \\ &\frac{1}{\sqrt{\left| {{u}_{1}}{{u}_{2}} \right|}}\int_{-\infty }^{+\infty }{\int_{-\infty }^{+\infty }{\frac{x-{{v}_{1}}}{{{u}_{1}}}}}, \frac{y-{{v}_{2}}}{{{u}_{2}}}\text{d}x\text{d}y \\ \end{align} $
(1) 在频率域表示为:
$ \begin{align} &{{\mathit{\boldsymbol{W}}}_{f}}\left( {{u}_{1}}, {{u}_{2}}, {{v}_{1}}, {{v}_{2}} \right)=\text{DWT}\left[ \mathit{\boldsymbol{F}}\left( \eta , \zeta \right) \right]= \\ &\frac{1}{\sqrt{\left| {{u}_{1}}{{u}_{2}} \right|}}\int_{-\infty }^{+\infty }{\int_{-\infty }^{+\infty }{\mathit{\boldsymbol{F}}\left( \eta , \zeta \right)}}{{\mathit{\boldsymbol{H}}}^{*}}\left( {{u}_{1}}\eta , {{u}_{2}}\zeta \right)\times \\ &\text{exp}\left[ \text{j2 }\!\!\pi\!\!\text{ }\left( {{v}_{1}}\eta , {{v}_{2}}\zeta \right) \right]\text{d}\eta \text{d}\zeta \\ \end{align} $
(2) 式中, (u1, u2)是伸缩因子,(v1, v2)是移位因子;F (η, ζ)是2维信号的频谱,H*(u1η, u2ζ)是小波谱,exp[j2π(u1η, u2ζ)]是相位因子。
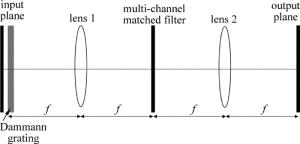
图像压缩方案如图 2所示。采用光学系统通过Dammann光栅上光学多通道系统的多参考匹配滤波器实现2维小波变换。将4副原彩色图像Om(x, y)(m= 1, 2, 3和4)先后通过空间光调制器输入系统并与Dammann光栅相乘,经过透镜后,能在透镜1的后焦平面上实现被复制频谱F (u, v)的2维阵列,然后经过第2个透镜的傅里叶变换作用,在输出面板上实现每个子小波的2维小波变换。由于每幅图像必须由相应的子小波处理,因此需要在第1个透镜的后焦平面上引入一个频谱阵列的多参考匹配滤波器(常见的小波函数的傅里叶变换均为正实值,而多参考匹配滤波器能由计算全息产生,并加载在空间光调制器上),该滤波器每个频谱对应一个不同子小波的傅里叶变换,每个频谱的位置与被复制的图像进行相应的位置匹配。因为输出面板是输入面板的一副图像,所有变换相互叠加起来,并行显示小波分解,所以用不同的参考光来对不同的子小波进行编码, 从而在输出面板上得到空分复用[16-17]。4个原始彩色图像可分别由光学系统分解,其公式如下:
$ \left\{ \begin{array}{l} {\mathit{\boldsymbol{k}}_1} = {\rm{DWT}}[{\mathit{\boldsymbol{O}}_1}(x, y)]\\ {\mathit{\boldsymbol{k}}_2} = {\rm{DWT}}[{\mathit{\boldsymbol{O}}_2}(x, y)]\\ {\mathit{\boldsymbol{k}}_3} = {\rm{DWT}}[{\mathit{\boldsymbol{O}}_3}(x, y)]\\ {\mathit{\boldsymbol{k}}_4} = {\rm{DWT}}[{\mathit{\boldsymbol{O}}_4}(x, y)] \end{array} \right\} $
(3) 式中, O1,O2,O3,O4是4个原始彩色图像, (x, y)表示图像的像素坐标,km(m=1, 2, 3, 4)是离散小波变换谱。最后在CCD上依次获取通过光学小波变换的图像并传输到计算机中。计算机通过使用低通滤波器来提取km的低频部分从而滤掉高频部分以获得4个滤波图像tmi(m=1, 2, 3, 4;i表示R, G, B)。为了减少传输通道和加密数据量,4个滤波图像的每个颜色分量在计算机中重新组合成三元组fi(x, y)(i=R, G和B)如图 1所示,表示为:
$ \begin{array}{l} {\mathit{\boldsymbol{f}}_i}(x, y) = \\ \{ {\mathit{\boldsymbol{t}}_{1i}}\left( {x, y} \right), {\mathit{\boldsymbol{t}}_{2i}}\left( {x, y} \right), {\mathit{\boldsymbol{t}}_{3i}}\left( {x, y} \right), {\mathit{\boldsymbol{t}}_{4i}}\left( {x, y} \right)\} \end{array} $
(4) -
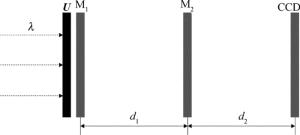
为了进一步提高明文的安全性,使用了一个菲涅耳衍射加密系统,如图 3所示。U代表要编码的三元组图像fi(x, y)(i=R, G和B),M1和M2代表两相位掩模,它们在[0, 2π]中是随机分布的,在统计上是独立的。产生波长为λ的准直平面波来照射系统,三元组图像fR(x, y), fG(x, y)和fB(x, y)依次经过菲涅耳衍射加密系统。经光学衍射加密系统编码后,由CCD相机记录衍射强度图案。
在图 3所示结构中, 入射到随机相位板M2的光波前可表示为:
$ \begin{array}{l} {\mathit{\boldsymbol{f}}_i}(\eta , \zeta ) = \frac{{{\rm{exp}}({\rm{j2 \mathsf{ π} }}{d_1}/\lambda )}}{{{\rm{j}}\lambda {d_1}}}\int {\int {{\mathit{\boldsymbol{f}}_i}} } (x, y){\mathit{\boldsymbol{M}}_1}\left( {x, y} \right) \times \\ [{\rm{exp}}\left[ {{\rm{j \mathsf{ π} }}{{(x - \eta )}^2} + {{\left( {y - \zeta } \right)}^2}]/(\lambda {d_1})} \right]{\rm{d}}x{\rm{d}}y \end{array} $
(5) 式中, $ {\rm{j}} = \sqrt { - 1} $,λ表示光波长,d1表示衍射距离, M1(x, y)是随机矩阵,(x, y)和(η, ζ)分别表示输入图像fi(x, y)(i=R, G和B)和M1的坐标。为简洁起见,将(5)式改写为:
$ {\mathit{\boldsymbol{f}}_i}(\eta , \zeta ) = {\rm{FT}}\left[ {{\mathit{\boldsymbol{f}}_i}(x, y){\mathit{\boldsymbol{M}}_1}\left( {x, y} \right);{d_1}} \right] $
(6) 因此,输出平面CCD所获取的强度图像可以表示为:
$ \begin{array}{l} {\mathit{\boldsymbol{C}}_i}\left( {\mu , \nu } \right) = \left| {{\rm{FT}}\left\{ {{\rm{FT}}} \right.} \right.\left[ {{\mathit{\boldsymbol{f}}_i}(x, y){\mathit{\boldsymbol{M}}_1}\left( {x, y} \right);{d_1}} \right] \times \\ {\left. {{\mathit{\boldsymbol{M}}_2}\left( {\eta , \zeta } \right);{d_2}\} } \right|^2} \end{array} $
(7) 式中, ||表示取模运算,(μ, ν)表示CCD平面的坐标, M2(η, ζ)是随机矩阵,图像Ci(i=R, G和B)是三元组图像fi(x, y)(i=R, G和B)对应的子密文,d1和d2分别表示M1到M2以及M2到CCD平面的衍射距离。彩色图像I(μ, ν)是组合图像Ci(i=R, G和B)最终的密文。
-
解密是加密过程的逆过程,如图 1b所示。首先,在计算机中将密文I (μ, ν)中提取Ci(i=R, G, B)后, 将Ci(i=R, G, B)传播回菲涅耳衍射加密系统的输入面,计算公式如下:
$ \begin{array}{l} {\mathit{\boldsymbol{f}}_i}(\eta , \zeta ) = {\rm{IFT}}\left[ {{\rm{IFT}}\left( {{\mathit{\boldsymbol{C}}_i}\left( {\mu , \nu } \right)} \right.}, \right.\\ \;\;\;\left. {\left. { - {d_2}} \right]{\mathit{\boldsymbol{M}}_2}{{(\eta , \zeta )}^*}, - {d_1}} \right] \end{array} $
(8) 式中, *表示共轭。重建的图像fi(η, ζ)(i=R, G和B)是彩色密文的解密图像的三元组。然后,原始彩色图像Om(m=1, 2, 3, 4)可以通过重构从fi(η, ζ)(i=R, G和B)的R,G和B分量来解密出原始图像。
-
为了检查作者所提出的方案的性能,使用MATLAB进行了几个数值模拟。在本节中,从统计特性,密钥空间和一些攻击方面来分析加密方案的安全性,并分析评估解密图像的质量。
-
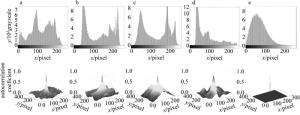
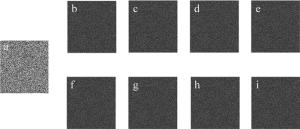
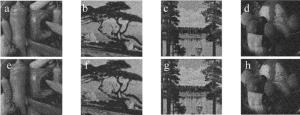
图 4a~图 4d中是4副彩色原始图像,分别为“peppers”, “tree”, “lake”, “fruits”,其大小为256×256像素。计算机模拟中,光波波长λ=632.8nm,衍射距离为d1=d2=50mm。图 4e~图 4g分别为图像fi(x, y)(i=R, G和B)对应的加密图像,其像素大小为128×128。图 4h是将3幅R, G, B分量在计算机中合成为一副彩色密文I (μ, ν),其大小为256×256像素。从密文I (μ, ν)可以看出,原多幅彩色图像的信息加密成了单幅彩色密文,极大地减少了数据量。Cxy值通常被广泛用作评估图像质量的客观测量,其值在0和1之间。它们的值越接近1,恢复图像的质量越好。
$ {C_{xy}} = \frac{{\sum\limits_{l = 1}^L {\left\{ {\left( {{x_l} - \frac{1}{L}\sum\limits_{l = 1}^L {{x_l}} } \right) - \left( {{y_l} - \frac{1}{L}\sum\limits_{l = 1}^L {{y_l}} } \right)} \right\}} }}{{\sqrt {\sum\limits_{l = 1}^L {{{\left( {{x_l} - \frac{1}{L}\sum\limits_{l = 1}^L {{x_l}} } \right)}^2}} } \sqrt {\sum\limits_{l = 1}^L {{{\left( {{y_l} - \frac{1}{L}\sum\limits_{l = 1}^L {{y_l}} } \right)}^2}} } }} $
(9) 式中, xl和yl是图像中两个相邻像素的值,并且L是图像像素点的总数。图 5a~图 5d所示是对应的解密图像,其大小为128×128像素,相对于应的Cxy值分别为0.9913, 0.9936, 0.9970和0.9950。从表 1可以看出, 与参考文献[18]中的解密图像质量对比,本文中提出的加密算法提高了解密图像的质量。
Table 1. Cxy values of the decrypted images
Cxy values peppers tress lake fruits the proposal 0.9939 0.9960 0.9833 0.9974 reference [18] 0.9411 0.8746 0.8512 0.8574 -
通过计算图像加密前后的灰度直方图和加密图像与原始图像之间的相关性,可以分析加密算法抵抗统计攻击的能力。
图 6a~图 6d上面的小图分别是原图“peppers”,“trees”,“lake”和“fruits”的灰度直方图, 图 6e上面的小图是当4个图像被加密成一副密文的直方图。显然,加密图像的直方图与原始图像的直方图显著不同。同时也说明加密前后图像的统计信息是完全不同的,即原始图像信息不能通过统计法从加密图像中获得。
图 6a~图 6d下面的小图分别是原图“peppers”,“trees”,“lake”和“fruits”的相关性图,图 6e下面的小图表示加密后的彩色密文图像的自相关性图。可以发现,原始图像的相邻像素高度相关,而加密图像的相邻像素之间的相关性非常小。这两个测试表明,未经授权的用户不可能通过统计分析方法获得原始图像的有效信息。因此,该方案能有效抵抗统计分析的攻击。
-
一些攻击,如已知明文攻击,选择明文攻击和选择密文攻击,常被用来评估加密系统的安全性。本文中提出的用小波变换和菲涅耳变换相结合的方案在抵抗噪声和遮挡攻击方面起着重要的作用。
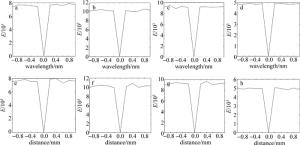
在菲涅耳衍射系统中,波长λ和衍射距离d1和d2被认为是解密的密钥。为了评估这些密钥的性能,本文中给出解密的彩色图像相对于波长λ和衍射距离d(d1,d2)的偏差Δλ(20nm)和Δd(20mm)的均方差曲线E,如图 7a~图 7h所示。图 8b~图 8i分别是从图 8a中相应的具有不正确波长(λ+Δλ)和衍射距离(d1+ Δd)的解密图像。从图 7中可以看出E值在正确的密钥周围急剧变化,从解密的图中看不到原始彩色图像的任何信息,这意味着本文中提出的加密系统有着高度安全性。公式如下:
$ E = \frac{1}{{MN}}\sum\limits_{x = 1}^M {\sum\limits_{y = 1}^N {\mathit{\boldsymbol{Y}}\left( {x, y} \right) - \mathit{\boldsymbol{X}}(x, y){]^2}} } $
(10) 式中, Y (x, y)和X (x, y)表示位置(x, y)处的恢复图像和原始图像的像素值,M和N分别表示图像的高度和宽度。
-
在图像存储和传输中,密文图像不可避免地受到噪声污染以及数据的丢失。因此,需要通过考虑加密图像中的椒盐噪声来测试所提出的抗噪声攻击的能力。按照参量k调整不同强度的椒盐噪声,如下所示:
$ I' = I(1 + kG) $
(11) 式中, I′表示受噪声影响的加密图像,k是表示噪声强度的系数,G是椒盐噪声。恢复的图像如图 9a~图 9h所示。Cxy值如表 2所示。从解密图像中几乎可以完全看到原始彩色图像的信息。可以得出结论,本文中的方法有很好的抗噪声攻击的能力。
Table 2. Cxy values of the decrypted images after noise
salt-and-pepper noise with different stand deviation Cxy values of decrypted images pepper tress lake fruits k=0.8 0.9180 0.9592 0.9538 0.9424 k=1 0.9035 0.9526 0.9470 0.9345 -
本加密方案的鲁棒性是通过遮挡攻击来分析的。图 10a和图 10f分别是加密数据被遮挡25%和50%的图,其解密图像分别如图 10b~ 图 10j。表 3为解密图像的Cxy值。可以看出,本文中提出的加密系统对于遮挡攻击具有一定的鲁棒性。
Table 3. Cxy values of the corresponding decrypted images after occlusion
occlusion of the encrypted image/% Cxy values of decrypted images pepper tress lake fruits 25% 0.6525 0.7702 0.7606 0. 7082 50% 0.3943 0.5383 0.5137 0.4685 -
设计了一种基于小波变换和菲涅耳变换的多彩色图像加密算法,能有效的解决多彩色图像加密后数据量大,传输速度慢的问题。本文中提出的方法不仅可以增加加密图像的容量,而且可以减少加密通道,大大降低加密系统的复杂度。该算法具有灵活性高、密钥敏感性强,且能有效抵抗分析攻击和统计分析等特点。
小波变换和菲涅耳变换的多彩色图像加密
Multiple-color-image compression and encryption by using discrete wavelet transform in Fresnel transform domain
-
摘要: 为了解决多彩色图像加密后,解密图像质量不佳、数据量大以及传输时速率慢的问题,采用了一种基于小波变换和菲涅耳变换的多彩色图像加密方法,加密过程中,利用小波变换的多级分解特性提取每幅彩色图像的低频分量,将低频分量分别重组为三元组图像(R,G和B),并且依次将三元组图像(R,G和B)通过菲涅耳域中的衍射加密系统,对这3个三元组图像进一步加密,从而实现了多彩色图像的加密。结果表明,该方法不仅可以高质量地恢复原始彩色图像,而且可以同时对4幅彩色图像进行加密,提高了加密彩色图像的容量;原始图像经过小波变换,其数据量压缩到原来的1/4,有利于数据的传输和存储。该算法能够有效地同时对多幅色彩图像进行压缩和加密,不仅提高了解密图像的质量,并且具有较高的密钥敏感度和较好的鲁棒性。Abstract: In order to solve the problems of the low quality of image, the large amount of data and the slow rate of transmission, an optical compression and encryption method of multiple-color images by using discrete wavelet transform in Fresnel transform domain had been proposed. In the process of encryption, the low-frequency components of each color image were extracted by using the multilevel decomposition characteristics of wavelet transform, and the low frequency components were reorganized to triplet images (R, G and B), respectively. And the triplet images (R, G and B) were sequentially encrypted through the diffraction encryption system in the Fresnel domain. After triplet images were further encrypted, the encryption of multi-color images was realized. The results show that, the method can not only reconstruct the original color image with high quality, but also encrypt 4 color-images at the same time, which increases the capacity of the encrypted color image. The data volume of the encryption is compressed 1/4 after wavelet transform, which is beneficial to the transmission and storage of the data. The algorithm can effectively compress and encrypt multiple-color images at the same time. It not only improves the quality of the decrypted image, but also has high key sensitivity and good robustness.
-
Table 1. Cxy values of the decrypted images
Cxy values peppers tress lake fruits the proposal 0.9939 0.9960 0.9833 0.9974 reference [18] 0.9411 0.8746 0.8512 0.8574 Table 2. Cxy values of the decrypted images after noise
salt-and-pepper noise with different stand deviation Cxy values of decrypted images pepper tress lake fruits k=0.8 0.9180 0.9592 0.9538 0.9424 k=1 0.9035 0.9526 0.9470 0.9345 Table 3. Cxy values of the corresponding decrypted images after occlusion
occlusion of the encrypted image/% Cxy values of decrypted images pepper tress lake fruits 25% 0.6525 0.7702 0.7606 0. 7082 50% 0.3943 0.5383 0.5137 0.4685 -
[1] JAVIDI B, REFREGIER P. Optical image encryption based on input plane and Fourier plane random encoding[J]. Optics Letters, 1995, 20(7):767-769. doi: 10.1364/OL.20.000767 [2] QIAO J P, DENG L W, HE J, et al. Optimization of fast image encryption algorithm based on chaotic mapping[J]. Laser Technology, 2017, 41(6):897-897(in Chinese). [3] LIU Z, LI S, LIU W, et al. Image encryption algorithm by using fractional Fourier transform and pixel scrambling operation based on double random phase encoding[J]. Optics and Lasers in Engineering, 2013, 51(1):8-14. doi: 10.1016/j.optlaseng.2012.08.004 [4] JOSHI M, CHANDRASHAKHER, SINGH K. Color image encryption and decryption using fractional Fourier transform[J]. Optics Communications, 2007, 279(1):35-42. doi: 10.1016/j.optcom.2007.07.012 [5] LIU H, WANG X. Color image encryption using spatial bit-level permutation and high-dimension chaotic system[J]. Optics Communications, 2011, 284(16):3895-3903. [6] WANG P, YUAN C J, WANG L, et al. Encryption and decryption for double images based on fractional Fourie transformation[J]. Laser Technology, 2014, 38(4):551-555(in Chinese) [7] SITU G, ZHANG J. Double random-phase encoding in the Fresnel domain[J]. Optics Letters, 2004, 29(14):1584-1586. doi: 10.1364/OL.29.001584 [8] CHEN L, ZHAO D. Optical color image encryption by wavelength multiplexing and lensless Fresnel transform holograms[J]. Optics Express, 2006, 14(19):8552-8560. doi: 10.1364/OE.14.008552 [9] ABUTURAB M R. Optical interference-based multiple-image encryption using spherical wave illumination and gyrator transform[J]. Applied Optics, 2014, 53(29):6719-6728. doi: 10.1364/AO.53.006719 [10] CHEN W. Optical multiple-image encryption using three-dimensional space[J]. IEEE Photonics Journal, 2016, 8(2):1-8. [11] YUEN C H, WONG K W. A chaos-based joint image compression and encryption scheme using DCT and SHA-1[J]. Applied Soft Computing, 2011, 11(8):5092-5098. doi: 10.1016/j.asoc.2011.05.050 [12] SHI X, ZHAO D, HUANG Y, et al.Multiple color images encryption by triplets recombination combining the phase retrieval technique and Arnold transform[J]. Optics Communications, 2013, 306:90-98. doi: 10.1016/j.optcom.2013.05.041 [13] LIN C, WANG J G, MA W P, et al. Study on chaotic encryption algorithm for images after compression[J]. Microelectronics and Computer, 2013, 30(3):5-7(in Chinese). [14] XU G X, XU S Q, GUO X J, et al.Image compression-encryption algorithm combined DCT transform with DNA operation[J]. Laser Technology, 2015, 39(6):806-810(in Chinese). [15] MEHRA I, NISHCHAL N K. Wavelet-based image fusion for securing multiple images through asymmetric keys[J]. Optics Communications, 2015, 335:153-160. doi: 10.1016/j.optcom.2014.09.040 [16] MENDLOVIC D, OUZIELI I, KIRYUSCHEV I, et al. Two-dimensional wavelet transform achieved by computer-generated multireference matched filter and Dammann grating[J]. Applied Optics, 1995, 34(35):8213-8219. doi: 10.1364/AO.34.008213 [17] MENDLOVIC D, KONFORTI N. Optical realization of the wavelet transform for two-dimensional objects[J]. Applied Optics, 1993, 32(32):6542-6546. doi: 10.1364/AO.32.006542 [18] QIN Y, WANG Z, PAN Q, et al. Optical color-image encryption in the diffractive-imaging scheme[J]. Optics and Lasers in Engineering, 2016, 77:191-202. doi: 10.1016/j.optlaseng.2015.09.002 -

 网站地图
网站地图

 下载:
下载: